Industry-Leading
Vulnerability Management
Features
Prioritize Patching According to the Level of Risk
-
Effectively Identify
The database is not only fully aligned with the Common Vulnerabilities and Exposures (CVE) and National Vulnerability Database (NVD) but also provides in-depth information on a significant number of issues that are not reported by CVE/NVD. -
Deep Understanding
Gain access to extensive metadata, including information on exploits, methods of attack, and solutions if available. Enhance the understanding of risk by comparing the data with discussions among threat actors in Dark Web forums. -
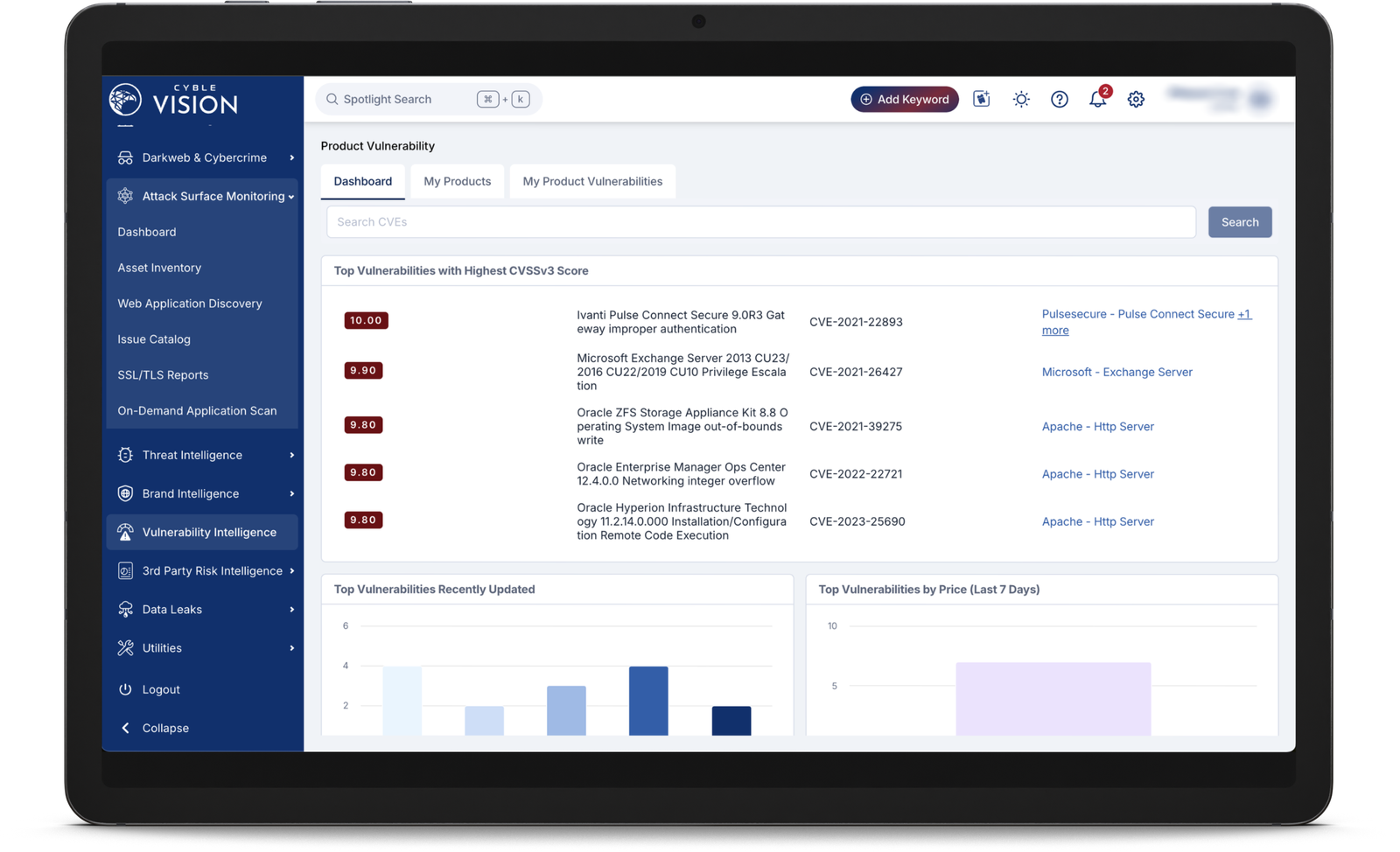
Product Vulnerabilities
Cyble's ability to quickly and accurately identify software vulnerabilities is an essential feature for organizations in the fight against cyberattacks. By staying ahead of potential security threats, organizations can minimize the risk of cyberattacks and ensure that their assets are protected. By identifying software vulnerabilities before they can be exploited by cyber criminals, organizations can take proactive measures to secure their systems and reduce the risk of data breaches or other types of cyber attacks. This not only helps to protect sensitive information, but also protects the organization's reputation and reduces the potential financial impact of a security incident.
-
Insights
Collaborate with top experts and receive support, a collaboration platform for Cyble analysts and clients. Stay ahead of the public by gaining early knowledge of exploits and taking prompt action. -
Asset Vulnerabilities
By staying ahead of potential security threats, organizations can ensure that their assets are protected and minimize the risk of data breaches or other types of cyber attacks. This not only helps to secure sensitive information, but also protects the organization's reputation and reduces the potential financial impact of a security incident. Cyble Asset Intelligence is a useful tool that helps organizations protect their assets from security threats by identifying and tracking vulnerabilities and allowing organizations to take proactive measures to address these vulnerabilities and prevent security incidents from occurring.
Vulnerability Management FAQs
Everything you need to know about the Vulnerability Management. Can’t find the answer you’re looking for? Please chat to our team.
Vulnerability Management is a continuous and regular process of detecting, evaluating, documenting, handling, and fixing cyber vulnerabilities across endpoints, workloads, and systems. Security teams usually utilize vulnerability management tools to find weaknesses and follow different procedures to patch or resolve them. An effective vulnerability management program employs threat intelligence and insights into IT and business operations to prioritize risks and address vulnerabilities promptly.
A vulnerability management system promptly identifies the most critical vulnerabilities. It incorporates contextual information, including business impact, exploitation potential, threat data, and risk factors, to provide recommendations for mitigating the identified issues.
A vulnerability management program constantly monitors, assesses, fixes, and reports vulnerabilities to assist organizations in handling security issues on a daily basis. It helps organizations swiftly detect vulnerabilities, prioritize and address the most pressing concerns, and ensure that significant weaknesses are not overlooked.
The identification of software vulnerabilities is a complex process that requires in-depth technical knowledge and expertise. Cyble uses advanced technologies and techniques to scan software and systems to identify any weaknesses or vulnerabilities that could be exploited by cyber criminals. This information is then analyzed and provided to organizations in a form that is easy to understand, allowing them to quickly assess the risk and take appropriate action to address the vulnerabilities. The database is fully aligned with the Common Vulnerabilities and Exposures (CVE) and National Vulnerability Database (NVD) but also provides in-depth information on a significant number of issues that are not reported by CVE/NVD.
The key steps in vulnerability management process include identifying vulnerabilities, assessing their impact, prioritizing remediation, applying fixes, and continuously monitoring for new threats.
Vulnerability management focuses on identifying, assessing, and mitigating risks, while patch management is a subset that involves applying software updates to fix vulnerabilities.
In 2025, tools offering advanced scanning, reporting, and risk prioritization are key for effective vulnerability management. Platforms like Cyble Vision stand out with capabilities that include monitoring vulnerabilities, providing actionable insights, and helping organizations reduce their attack surface efficiently.
Small businesses can use affordable tools, prioritize critical vulnerabilities, conduct regular scans, and patch systems promptly to manage vulnerabilities effectively.
Vulnerability Management Solutions help businesses identify, assess, and remediate security weaknesses in their systems. They enhance cybersecurity by automating risk detection and prioritizing threats based on severity.
Resources

Vulnerability Management
Data Sheets
Request a personalized demo and discover how our advanced threat intelligence can empower your organization’s cybersecurity strategy. Witness the integration of our solutions with your existing security tools and understand how we can help you navigate the complex landscape of cyber threats.

