Industry-Leading
Third Party Risk Management
Secure Your Business from Third-Party Vulnerabilities with Cyble's Third Party Risk Management Solutions
As businesses increasingly depend on external vendors and partners, third-party risks such as data breaches and supply chain disruptions pose significant threats. Cyble’s Third-Party Risk Management (TPRM) solution offers the tools, intelligence, and insights needed to protect your business from these risks while ensuring regulatory compliance.

Cyble Wins Global Infosec Award 2025 for Outstanding Third-Party Risk Management
How It Works
Gather
Cyble gathers intelligence from a wide range of sources, including vendor reports, cybersecurity monitoring tools, and real-time threat data, to monitor activities and risks across your third-party ecosystem. This data collection process is integral to Cyble’s Third-Party Risk Management (TPRM) strategy, ensuring comprehensive visibility into potential third-party risks.
Analyze
Using advanced machine learning and AI-powered algorithms, Cyble analyzes vendor risk data to uncover vulnerabilities, assess security postures, and identify emerging threats that could affect your business. This analysis is central to mitigating third-party risks and enhancing the effectiveness of our TPRM solution.
Evaluate
Cyble evaluates risks, vulnerabilities, and security gaps associated with your vendors, providing expert recommendations that help secure your supply chain. Our Third-Party Risk Management platform delivers SOC-vetted risk scores and offers actionable insights, making third-party risk management seamless and effective.
Deliver
Deliver High-quality, SOC-vetted risk scores are provided promptly, offering insights into critical risks such as compromised vendor credentials, data breaches, and potential supply chain disruptions. We display the quantum of data found and suggest the impact along with actionable recommendations, enabling your team to take swift, informed action. Cyble’s Third-Party Risk Management solution delivers comprehensive third-party risk mitigation.
Why Cyble’s Third-Party Risk Management Stands Out
End-to-End Risk Visibility
Advanced Threat Intelligence
Tailored Risk Assessments and Scoring
Mitigation Strategies and Actionable Insights
Compliance with Regulatory Requirements
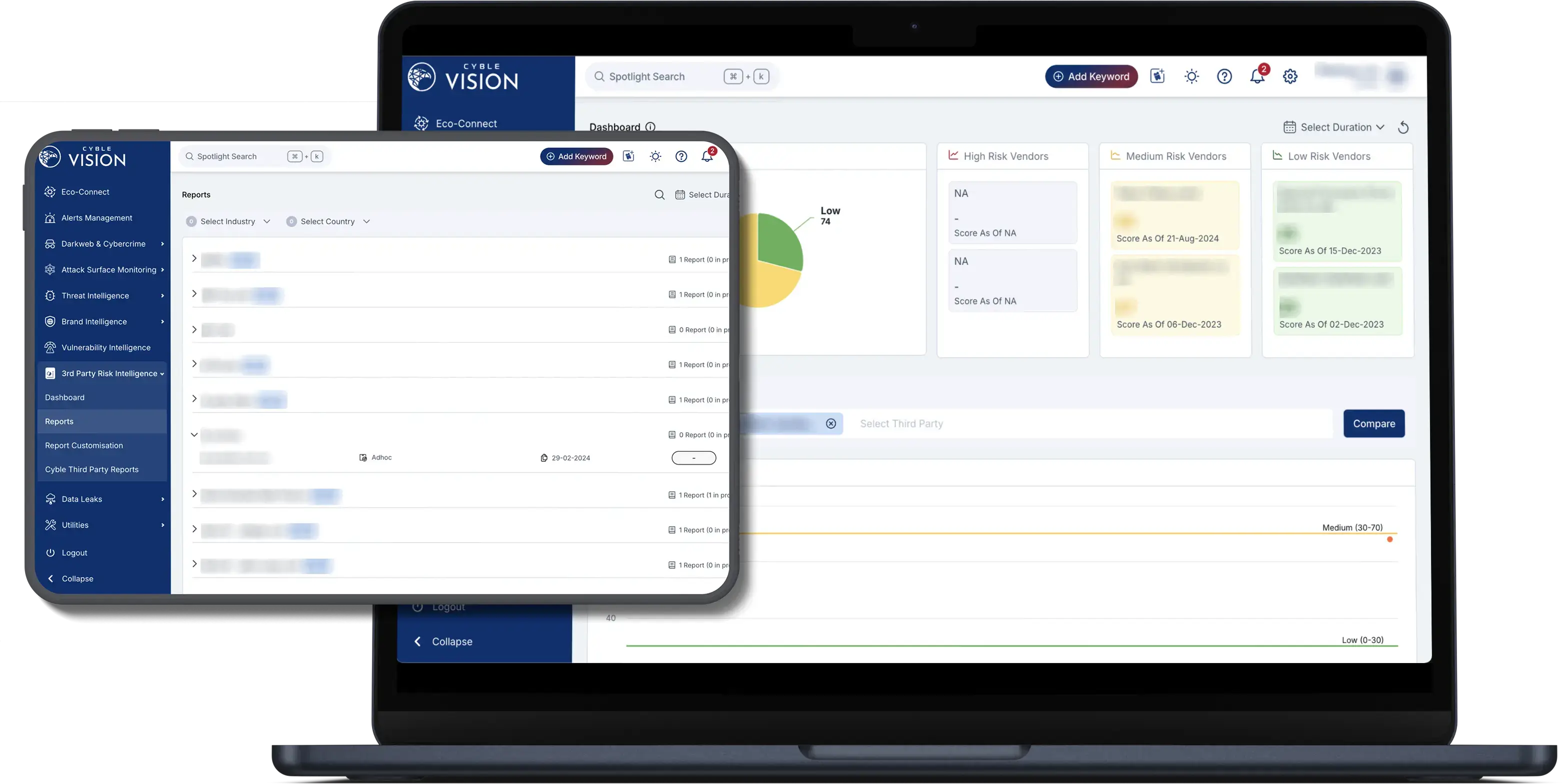
Key Benefits of Cyble's Third-Party Risk Management (TPRM) Solution
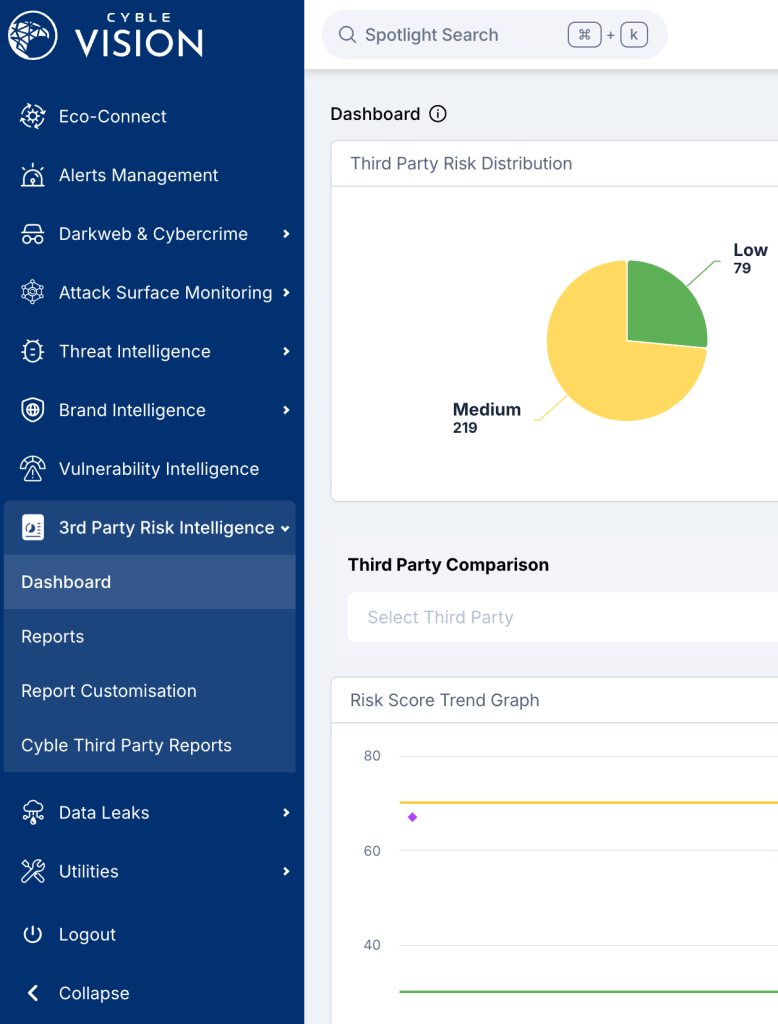
-
Real-Time Threat Detection
Get instant notifications when a third-party vendor is exposed to a potential threat, ensuring proactive management of third-party risks.
-
Centralized Risk Management
Manage all your third-party relationships and associated risks in one easy-to-use platform.
-
Data-Driven Decisions
Leverage comprehensive risk scoring and detailed vendor reports to make informed decisions that protect your business from third-party vulnerabilities.
-
Faster Response to Risks
Cyble’s Third-Party Risk Management solution ensures that you can respond quickly and effectively to vendor-related risks with actionable strategies.
Resources

Third Party Risk Management
Data Sheets
Third Party Risk Management FAQs
Third-party risk management (TPRM) is the process of assessing, monitoring, and mitigating risks associated with external entities that your organization works with. These third parties may have access to sensitive data or provide critical services, and TPRM helps ensure that their involvement doesn’t pose unacceptable risks to your business.
Third-party risk refers to potential threats or vulnerabilities that arise when an organization engages with external entities, such as vendors, suppliers, or service providers. These risks can include security breaches, data leaks, operational disruptions, or regulatory non-compliance.
The third-party risk management process involves identifying third parties, assessing the risks they may introduce, monitoring their activities, and taking steps to mitigate those risks. This process typically includes risk assessments, due diligence, ongoing monitoring, and implementing control measures to ensure compliance with the organization’s risk appetite.
A third party is any external organization directly engaged by your business, such as a vendor or supplier. A fourth party, on the other hand, is a subcontractor or another external entity that your third-party provider relies on to deliver their services. In other words, fourth parties are indirectly involved in your business operations through your third parties.
To create a third-party risk management program, start by identifying all the third parties your organization works with. Then, assess the risks they may pose by evaluating factors like their access to sensitive data, regulatory compliance, and operational reliability. Develop a risk assessment framework, establish monitoring protocols, and implement controls to mitigate these risks. Regularly review and update the program to address new risks and ensure ongoing compliance.
Key steps include identifying third-party vendors, assessing risks, defining control requirements, monitoring compliance, and continuously evaluating risks over time.
Organizations use tools like questionnaires, audits, and continuous monitoring to evaluate vendors’ security practices and compliance with regulations.
Challenges include lack of visibility into vendor security, regulatory compliance, and communication gaps. These can be overcome by conducting thorough vendor assessments, leveraging automated risk management platforms, and enforcing strict contracts and policies.
Cyble Vision helps organizations assess and manage third-party risks by offering insights into the security status of vendors and partners. It enables businesses to identify potential vulnerabilities in the supply chain and take necessary steps to mitigate risks.

