Cyble Executive Monitoring
Secure Your Leadership, Safeguard Your Organization
Why Settle for Reactive Measures?
At Cyble, we believe in proactive defense. With Cyble’s Executive Monitoring, you gain access to a unified platform designed to detect threats early, alert key personnel in real time, and take decisive action—keeping your leadership secure wherever they are.
How it Works
A Comprehensive Solution to Strengthen Your Cloud Security
-
Social Media Monitoring
Detect and eliminate fake profiles with instant alerts, swiftly addressing impersonations to protect brand reputation. -
Takedown Service
Eliminate fraudulent websites and pages in real-time. -
PII and Credential Monitoring
Monitor dark web forums and cybercrime platforms for PII leaks and compromised credentials.
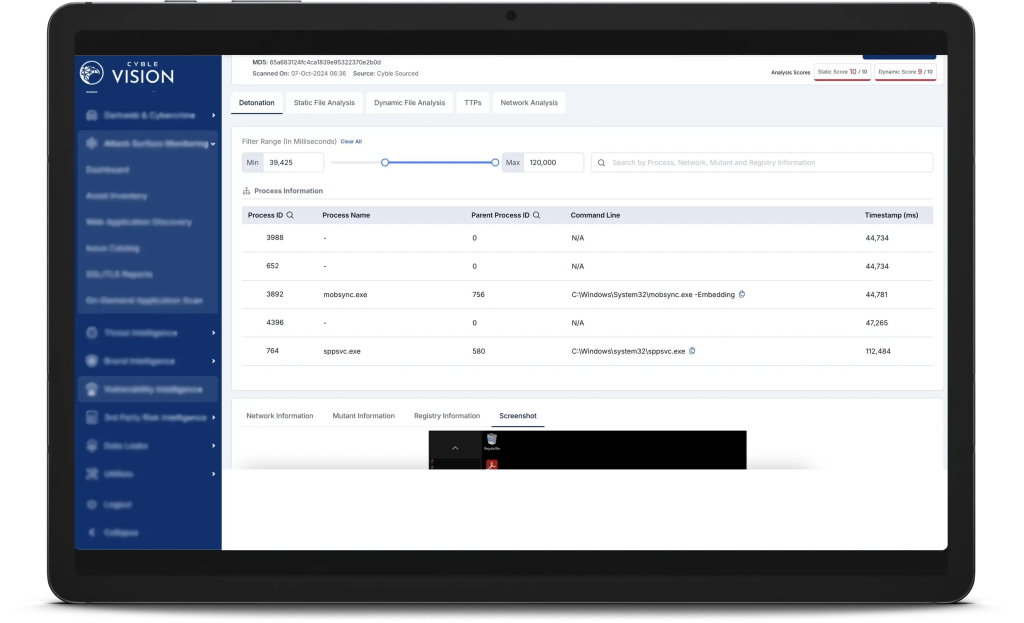
Centralized Control for Instant Decision-Making
Customizable Alerts
Receive notifications tailored to your preferences—via email, WhatsApp, or SMS.
Actionable Insights Dashboard
Manage risks with a single platform offering real-time intelligence and data-driven insights.
Seamless Integration
Enhance physical and digital threat monitoring with Cyble’s executive surveillance suite.
Deepfake Detection
Advanced Monitoring
Prompt Alerts
Get timely notifications of suspected deepfake content, allowing quick action to protect personal privacy, corporate reputation, and public trust. Stay ahead of threats with timely alerts, ensuring enhanced social media security and effective risk mitigation.
Take Control with Cyble Executive Monitoring
Executive Monitoring FAQs
What is Executive Monitoring?
Why is Executive Monitoring important?
Why choose Cyble’s Executive Monitoring?
- Instant alerts to prevent incidents in real-time.
- Advanced dark web monitoring to track data leaks.
- Takedown services for fraudulent pages and sites.
- Customizable notifications for travel-related risks.

